3.12.1 Authentication
The Authentication object allows a system that stores usernames and/or passwords to share them with other applications through SIF. The provider of the Authentication object may only support providing a username or a password, or it may support both.
The Authentication object is also able to transmit a user's network identity through SIF. If the user has an account in a network directory system that supports LDAP, the user's distinguishedName or username is shared to uniquely identify the user to applications that support LDAP or native network authentication options.
Details of how to implement the password element are included below the object definition.
SIF_Events are reported for this object.
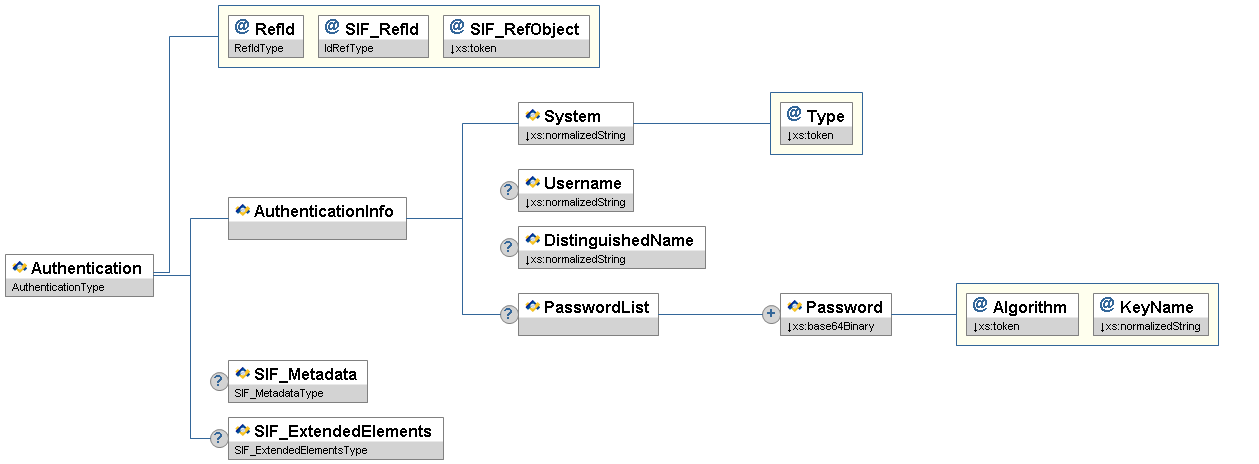
Figure 3.12.1-1: Authentication| Element/@Attribute | Char | Description | Type | |||
|---|---|---|---|---|---|---|
| Authentication | The Authentication object allows a system that stores usernames and/or passwords to share them with other applications through SIF. The provider of the Authentication object may only support providing a username or a password, or it may support both. The Authentication object is also able to transmit a user's network identity through SIF. If the user has an account in a network directory system that supports LDAP, the user's distinguishedName or username is shared to uniquely identify the user to applications that support LDAP or native network authentication options. | |||||
@ | RefId | M | The SIF RefId that uniquely identifies this authentication object. | RefIdType | ||
| @ | SIF_RefId | M | The SIF RefId of a student or staff member | IdRefType | ||
| @ | SIF_RefObject | M | The type of SIF object that the SIF_RefId attribute identifies. | values:
| ||
| AuthenticationInfo | M | The authentication information for one system. | ||||
| AuthenticationInfo/System | M | An identifying string for the system that supports this authentication information. | xs:normalizedString
| |||
| @ | Type | M | Specific type of user identification. | values:
| ||
| AuthenticationInfo/Username | O | The identification string for this user. | xs:normalizedString
| |||
| AuthenticationInfo/DistinguishedName | O | This is the distinguished name of the user in a network directory system. | xs:normalizedString
| |||
| AuthenticationInfo/PasswordList | O | Allows a provider or publisher to specify the same password using multiple algorithms, if supported. | List | |||
| AuthenticationInfo/PasswordList/ Password | MR | A representation of the user's password using the given algorithm. | xs:base64Binary
| |||
| @ | Algorithm | M | The method used to encrypt the user's password. See the implementation details below. | values:
| ||
| @ | KeyName | M | The name of the key to be used for decryption of the password. Left blank for plain, encoded text (Algorithm attribute value of "base64") and hash algorithms. | xs:normalizedString
| ||
| SIF_Metadata | O | SIF_Metadata | ||||
| SIF_ExtendedElements | O | SIF_ExtendedElements |
3.12.1.1 Password Implementation Details
While Authentication objects transported over SIF HTTPS are typically secure in transit, SIF objects are often stored in logs and databases. If the network infrastructure is not secure, the passwords could be subject to snooping from system users. Because of this, the design of the Authentication object requires that passwords never be transmitted in plain text, to prevent casual viewing. The design of this object allows passwords to be securely encrypted using a variety of encryption algorithms.
Passwords in the Authentication object can be shared in one of three ways as documented in the sections below.
3.12.1.1.1 Encoded Text
Sharing a password using encoded text is a very insecure method, because it uses a well-known algorithm and the value is not encrypted. The only merit of using this method is that the password is not readable as plain text, and thus deters any casual attempt to read a password. To share passwords in this manner, the following steps must be followed:
-
The publishing agent creates a
Passwordelement with the algorithm set tobase64. - The agent encodes the Unicode representation of the password using the UTF-8 encoding.
- The resulting binary value is then base64 encoded.
-
Write the result as the payload of the
Passwordelement.
3.12.1.1.2 Hashed Text
Sharing a hashed text version of a password means that the original password is not shared. Clear text passwords are not retrievable from values stored as hashes. These hashed values can only be used to verify passwords input by a user.
What is shared is a cryptographically secure hash of the password. This hash allows other applications to verify a user's password when s/he logs in by comparing the hash value, not the original password. To share passwords in this manner, the following steps must be followed:
-
The publishing agent creates a
Passwordelement with the algorithm set toMD5orSHA1. - The agent encodes the Unicode representation of the password using the UTF-8 encoding.
- Hash the resulting binary value with the chosen hash algorithm.
- Encode the binary result using base64 encoding.
-
Write the result as the payload of the
Passwordelement.
3.12.1.1.3 Encrypted Text
Sharing a password using encrypted text can be very secure.
The key being used to encrypt the data should be known only to the applications.
The KeyName attribute is used to allow agents to uniquely identify keys that are being used.
To share passwords in this manner, the following steps must be followed:
-
The publishing agent creates a
Passwordelement with the algorithm set toDES,TripleDES,RC2, orAES. - The agent encodes the Unicode representation of the password using the UTF-8 encoding.
- Generate a cryptographically secure Initialization Vector (IV).
- Configure the encryption algorithm to use a cipher mode of CBC.
- Configure the encryption algorithm to use a block size of 64 bits (8 bytes).
- Configure the encryption algorithm to use the generated IV.
- Configure the encryption algorithm to use the specified key for encryption.
- Configure the encryption algorithm to use PKCS#7/PKCS#5 padding mode.
- Encrypt the binary representation of the password that was generated in step 2.
- Encode the binary result using base64 encoding.
-
Write the result as the payload of the
Passwordelement.
3.12.1.1.3.1 Example Keys
The XML in the Authentication example can be used to verify an agent's implementation of any of the published algorithms.
The password being shared for the sake of the example is ¿sècrèt.
High-Unicode characters are being used in this example to validate proper encoding.
The actual Unicode characters are: U+00BF, U+0073, U+00E8, U+0063, U+0072, U+00E8, U+0074.
The encryption keys being used are as follows (in base 64 format)
| Key Name | Key (in base64 format) |
| 64-BIT_KEY | dW7SKzwdn0Q= |
| 128-BIT_KEY | TcdilmUZ6qvbmegl2it2pA== |
| 192-BIT_KEY | mECbXMo+fOMWRwam7tyUEE59jbO9O0Z4 |
NOTE: Real-world implementations of password sharing should use keys other than the ones used for this documentation. These keys are provided for example's sake only. Keys should be generated using a secure cryptographic key generator.