
The following assumptions are made of non-technical readers of this specification, especially end users undertaking SIF implementations:
They should also be aware that there are numerous third-party products and services available to aid in SIF implementation and integration.
Technical readers implementing SIF software and software solutions, particularly those implementing SIF Agents and Zone Integration Servers from scratch as opposed to using or building upon third-party products and services, should have an understanding of:
It is furthermore assumed that implementers have at their disposal or can implement:
Implementers are referred to Notes on Related Technologies, which highlights technologies leveraged within SIF or related to SIF, either in their entirety or as a subset. This partially normative appendix points out specifics casual readers of referenced documents on these technologies must not ignore when implementing SIF Zone Integration Servers and Agents.
This section presents the ideas behind the implementation of SIF, including the application and data models on which it is based. It serves as a precursor to further descriptions in following sections.
The data that can be exchanged in SIF is defined using a series of data objects.
These objects are expressed using [XML] and are defined structurally by this document and associated schemas,
with this document and supporting documentation defining the semantics behind the exchange of individual data objects.
StudentPersonal, StudentSchoolEnrollment and StaffPersonal are three of the many predefined data objects.
Although there are many variations of SIF topographies, the common feature is that a number of applications wish to share data. All SIF implementations, regardless of their complexity, consist of one or more applications with their associated agents communicating via a Zone Integration Server (ZIS).
One typical use of SIF is to connect products from various vendors together within a single school. These applications could include a student information application, a food service program, and a library automation application. Each of these applications has a vendor-provided interface program called an Agent.
Since the same school shares these applications, it makes sense to group them together into a logical entity. This entity is referred to as a Zone and is managed by a Zone Integration Server (ZIS).
There are no predefined sizes for zones, so a zone can be as large or small as required in order to meet the needs of the customer.
An application relies on its agent to exchange data using a predefined data model. Agents then communicate with other agents using the ZIS as a routing resource. The ZIS also provides access control so the customer can control which applications have access to which SIF data.
The Zone is the primary means of partitioning data, applications, and policies. Zones are typically organized around geographic boundaries (e.g. school, district, region, state) or functional boundaries (e.g. horizontal integration, student locator services, data warehousing and reporting services). A SIF Context offers the ability to further partition the data within a Zone, to offer different perspectives of the data based on customer needs and application abilities. For example, while a student information system typically serves as the source for student-related data in the default context of a zone that integrates applications in a school or district, a data warehouse might better be suited to provide a historical or longitudinal perspective of that exact same student data in a different context, a context more suited to the reporting and data warehousing needs of an implementation. Contexts enable customers and system integrators to work with data in new ways while retaining the zone topologies commonly in use in implementations.
In addition to offering different perspectives on a zone's data, contexts allow two or more agents to
register as a provider of the same object type within a zone. This may lead to future solutions built around
contexts; for example, to better define how systems that publish similar objects cooperate in the same zone
(e.g. student information systems and special education packages). Contexts also make it easier to apply a
different set of business rules to different audiences.
Unlike zones, which can be named and assembled in a variety of ways at the discretion of system integrators,
contexts are to be treated as a part of the specification. The SIF Association sanctions contexts
and provides documentation that defines each context's purpose and any associated
message choreographies and business rules for it. Contexts defined by the SIF Association have context names that begin with
SIF_ and the default context for a zone is named SIF_Default. It is RECOMMENDED
that all ZIS implementations support the SIF Association-defined contexts
as they are introduced; support for user-defined contexts is strictly implementation dependent, and agents are discouraged
from relying on ad hoc or user-defined contexts.
Agents share data in a Zone via two models, the Publish/Subscribe model and the Request/Response model. Agents publish data changes
of interest to subscribers by sending a SIF_Event message to the ZIS. Agents can also request or query data from
other agents in a Zone by sending a SIF_Request message to an Agent, eventually being sent one or more SIF_Response
messages in return. This exchange of messages over a SIF-defined transport layer, SIF HTTPS or SIF HTTP, is the primary feature
that defines the SIF Infrastructure. Every message exchanged over this infrastructure is wrapped inside a SIF_Message and
contains a SIF_Header element that specifies the source of the message and optional security, destination and
context information. In addition to the messages exchanged between Agents via the ZIS, the SIF Infrastructure defines a number of messages
that are exchanged between Agent and ZIS, and between ZIS and Push-mode Agent—these serve primarily to register various Agent settings
at the ZIS and to support the exchange of messages between Agents.
When an application (the Requester) wants to gather data from a specific data object,
a SIF_Request message is sent to ZIS. The application may direct this request to a given Responder by specifying
an Agent ID in the SIF_DestinationId element of SIF_Header.
In most cases, however, the SIF_DestinationId element
is omitted in which case the ZIS routes the request to the default responder,
or Provider, for the data object of interest. Agents register as
Providers with the ZIS using either the SIF_Provision or SIF_Provide message.
There is a single Provider per object per context per zone. There may be multiple Responders for a given object in a zone context.
In order to maintain control over what data is exchanged over the zone and who exchanges it, the ZIS must provide an access control system that limits who can provide, request, and respond to requests for which data objects. The access control system must maintain policies for each registered application.
If the requester knows or wants to control who the responder
will be, it must place the responder's agent identifier in the
SIF_DestinationId element of the header of the SIF_Request message. The
ZIS will examine the SIF_Request message's header. If a SIF_DestinationId
element is present, the ZIS must route the SIF_Request to the specified agent/application subject to the limitations
imposed by the access control security policies for the zone. For instance, even though an application specifies that it wishes a specified application to respond, the zone security policy may prohibit the specified application from generating SIF_Response messages.
An application that wants to provide access to the data it
contains via SIF may function as a responder. Such applications will
support one or more SIF data objects. The application listens for
SIF_Request messages for the objects that it supports. When it receives a
SIF_Request for a supported object, the application will generate one or more
SIF_Response messages containing the application's data, which will be routed
by the ZIS to the requester. The responder must place the requester's agent identifier in the SIF_DestinationId element of the header for each SIF_Response message generated.
When an application receives a SIF_Request for a data object
that it does not support, it must return a SIF_Response message with the SIF_Error element populated to indicate the nature of the error (invalid object), a SIF_PacketNumber of 1 and the SIF_MorePackets element set to indicate that no further packets will be sent in response to the SIF_Request.
Applications propagate data updates by publishing SIF_Event
messages for the SIF data objects that are being added, changed, or
deleted. In order for an application to receive these SIF_Events,
subscriptions for the SIF data objects of interest must be entered at the ZIS.
This subscription process is performed when an application sends a SIF_Provision message or one or more SIF_Subscribe messages to the ZIS.
Once the subscriptions are entered, any SIF_Events for those objects received by the ZIS will be routed to the list of subscribers for those objects.
Once an application successfully sends a SIF_Event to the ZIS, the ZIS is responsible for delivering that SIF_Event to the subscribing parties
without any further communication to the SIF_Event originator.
The SIF_Event originator does not know how many applications, if any, receive the SIF_Event.
No notifications are provided to the originator to indicate whether a SIF_Event was delivered to a subscriber or not.
The ZIS must maintain an access control system that limits who can publish and subscribe to events for which data objects.
Before an application can utilize the services of the ZIS,
the application must register itself by sending a SIF_Register message
to the ZIS. Once registered, an application does not have to
perform any additional registration with the ZIS in order to be a publisher of
SIF_Event data. Any application that has registered itself with the ZIS may publish SIF_Events subject
to the limitations imposed by the access control security policies for the zone.
It is recommended that event publishers register their ability to publish events by using the SIF_Provision message.
Multiple applications may publish SIF_Event messages for a given data object.
The application that is registered as the Provider for a
given data object must be able to subscribe to SIF_Events for
that object but the application is not required to subscribe to SIF_Events in a given SIF implementation.
An application that has subscribed to a SIF_Event must
attempt to process the SIF_Event according to the business rules of the
application. If the SIF_Event contains insufficient information or
information that is inconsistent with the application's business rules, the
application may ignore the message.
If an application publishes a SIF_Event as a result of
changing the data within the application and the ZIS rejects the SIF_Event
message, it is recommended that the application rolls back or cancels
the changes that were made, but the application does not have to roll back the changes.
For example, an application may attempt to add a new student and publish a SIF_Event to reflect the addition.
If the application does not have permission to publish SIF_Event messages for that type of object, the SIF_Event is rejected.
The application does not have to remove the newly added student from its local database.
In order to ensure scalability and reliability, SIF requires that its request/response and publish/subscribe models be asynchronous in nature. Once a ZIS synchronously acknowledges receipt of a SIF_Event, SIF_Request or SIF_Response with the return of a successful SIF_Ack, an agent cannot be assured that these messages will immediately be delivered to subscribers, providers/responders or requesters, respectively, or that it will receive an immediate SIF_Response to any submitted SIF_Request.
The asynchronous communication model can be likened to communicating with someone via e-mail or through the postal office: an individual sends the message, but does not know when it will be received, much less when the receiver will respond.
By requiring asynchronous communications, a SIF implementation can exploit software designs that achieve high scalability and reliability. For example, even if an agent is not currently connected to a Zone, another application's agent can still send messages to that agent knowing that the ZIS will deliver those messages as soon as the agent is available.
In contrast to the asynchronous communication model, most agent-to-ZIS and ZIS-to-agent communication—over currently defined transport layers—is synchronous in nature. Any time an agent sends a SIF_Message to a ZIS, the agent waits for a SIF_Ack to be returned from the ZIS to acknowledge receipt of the message. Once acknowledged, the ZIS guarantees future delivery of SIF_Event, SIF_Request and SIF_Response messages, barring certain error conditions. For messages not directly related to the request/response and publish/subscribe models, the acknowledgement from the ZIS also indicates successful completion of operations related to registration, subscription, provision and system control operations. Relatedly, when a ZIS contacts an agent in Push mode, the ZIS waits for a SIF_Ack to be returned from the agent to acknowledge successful delivery of the message currently pending for the agent.
The security model of SIF centers around three areas: encryption, authentication and access control. SIF provides application agents the ability to specify the encryption and authentication requirements for all other agents that eventually come into contact with their sensitive data. Various communication protocols over which SIF data may be transferred, including SIF HTTPS, provide built-in support for easing the implementation details of guaranteeing encryption and authentication requirements. In addition, access control at the ZIS allows a zone administrator complete control over which agents are allowed to communicate which data to other agents.
As SIF HTTPS is the default communication protocol that all agents and ZIS implementations must support, many of the encryption and authentication levels specified in this document are tailored to the encryption and authentication algorithms currently defined within SIF HTTPS. When a ZIS implementation supports other communication protocols, the ZIS must guarantee that these levels are accurately reflected and adhered to when communicating with agents that support these same protocols.
Encryption provides the mechanism to ensure that only the sender and receiver of a message can view the message contents. In a totally secure model, all communications between agent and ZIS will be encrypted. The SIF HTTPS protocol, which must be supported by all agents and ZIS implementations, is a secure transport and provides encryption of the data being exchanged.
If additional communication protocols, or transports, are used, it is important to know if these transports are secure to avoid exposing sensitive data. SIF provides a method for an agent to specify to the ZIS how secure the channel between the ZIS and other agents must be when ultimately delivering the originating agent's sensitive data. ZIS implementations must guarantee the requested security levels when communicating with recipient agents, regardless of which transport is in use. If a ZIS is unable to ensure these security levels when communicating with a recipient agent, the ZIS must not transport the message across the insufficiently secure channel. It is recommended that the ZIS log the inability to deliver the message to the recipient agent due to security requirements.
The responsibility for guaranteeing the security of data that an originating agent transfers to the ZIS lies ultimately with the originating agent, or zone administrators. For example, if the originating agent requires a very secure channel for a given message, it should not intentionally or inadvertently communicate that message to the ZIS over an insecure or insufficiently secure channel, should the ZIS support such channels. At that point, the data has already been communicated insecurely. Zone administrators can prevent such occurrences by configuring the ZIS and agents within the zone such that a minimum security level is maintained, below which communication is impossible.
In many cases, the establishment of a secure channel and encryption can be delegated to the transport layer.
The role of authentication is to provide a means to ensure that the author of a message is the actual author. Authentication guards against a situation where a foreign agent claims to be a legitimate zone participant and fakes a message to gain access or alter the SIF data.
Another important role of authentication is to provide the ability to detect that each message that passes through the Zone arrives at its destination unaltered by other intermediaries.
Authentication support is optional but highly recommended.
SIF must be customizable for specific deployments. This particularly applies to customization for the security policies. For example, a SIF administrator can specify which applications can participate in the SIF deployment, which data objects each application can provide or request, and what events each application can produce and receive.
The access control requirements are discussed more fully under ZIS Requirements.
This section describes the architecture and components that make up SIF. It presents high-level functional requirements for each component and interfaces between them. More detail on particular requirements and interfaces may be found in Messaging and Infrastructure.
A SIF Zone is a distributed networking system that consists of a Zone Integration Server (ZIS) and one or more integration Agents. The size of a zone is flexible and could consist of a single building, school, a small group of schools, a district, a region, a state, a nation, etc. SIF is a scalable solution for data exchange. A SIF Implementation consists of one or more SIF Zones deployed and configured to meet customer data sharing and reporting needs.
A Zone Integration Server is a program that provides integration services to all the agents registered with it so that they can provide data, subscribe to events, publish events, request data, and respond to requests. It is responsible for all access control and routing within the Zone.
Each application requires an agent, which typically is provided by the application vendor, to communicate with other applications via the ZIS and their respective agents. For example, a school may use a student information application, a food service application, and a library automation application. Each of these applications must have an agent that acts as a go-between between the application and the Zone Integration Server.
In SIF, an agent never communicates with another agent directly. Instead, each agent communicates with the ZIS as a trusted intermediary that brokers the exchange of data with other agents. Having the ZIS manage routing responsibilities allows complex communications to occur between agents that have no direct information about each other and that may or may not be available for communication at any given point in time.
The following diagram illustrates a typical single-zone SIF implementation for a school.

A zone is often defined according to physical boundaries; for example, a zone can consist of all the applications that are connected over a private network and managed by one organization, such as a school. Security, scalability, and manageability requirements can also influence the decision of how zones are designed and configured.
Zones are a flexible and powerfully creative tool for meeting the data exchange and reporting needs of users; zones can be as varied as the customers in the education marketplace. While a single school zone may meet the needs of a single school, SIF implementations can scale to meet the needs of specific end users through the use of multiple zones, sometimes managed by different ZIS implementations. Two examples of many multiple-zone implementation design patterns are included here for illustration.
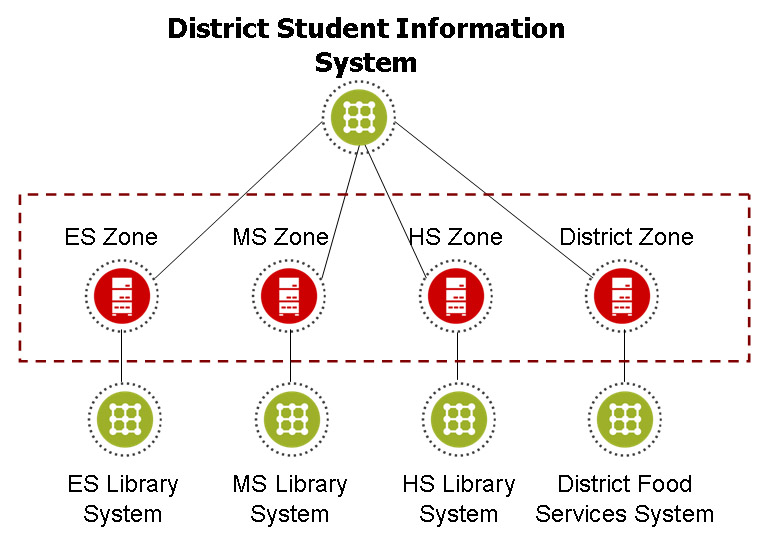
In the first, the data exchange needs of a district are met through the use of four zones, one for the district, and three for schools within the district: elementary, middle and high school. Here a student information system provides its complete set of district-wide data to a district zone, while providing school-based views of and access to that data in the individual school zones. Library systems in this implementation are school-based, while the food services system, like the SIS, is district-based.
The second example illustrates an agent communicating in both a district and a state zone. This agent could be associated with many different types of applications, including a SIS or data warehouse, reporting date up to the state, and so on.
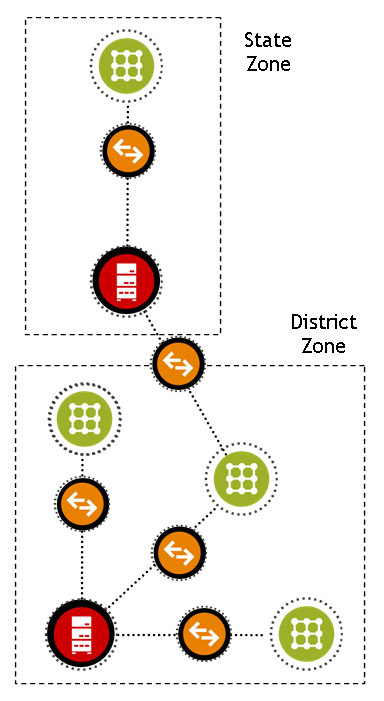
Multiply the district portion of this diagram by dozens or hundreds of districts, each with its own local zone or configuration of zones, and the distributed scalability of SIF using zones is readily apparent.
SIF requires that each agent and ZIS be identified with a distinct case-sensitive identifier that is unique within a zone.
This identifier is carried inside the SIF_SourceId element of the SIF_Header included in each SIF message and is used, among other
things, at the ZIS to reference access control permissions of each agent within the zone.
It is recommended that agent and ZIS implementations have user-configurable identifiers in order for zone administrators
to maintain unique identifiers within the zone.
The identifier should be descriptive of the role of the application in the zone. For example, the library automation agent for Ramsey Elementary might carry the identifier RamseyLib instead of the less descriptive CC41Agent. The Zone Integration Server for Ramsey might be known as RamseyZIS.
Data objects and the data local to an application that map to these objects often must be retrieved by a unique identifier. Likewise there often
exist relationships between data objects that require a unique key or identifier for efficient look-up of related data. SIF provides these keys
or unique identifiers through object identifiers, also known as RefIds or GUIDs thanks to SIF naming conventions and the
type of identifiers used in SIF, respectively.
The StudentPersonal object, for instance, carries detailed information about a student,
and most agents that manage or require student information
reference the data stored in this object and often map the RefId of StudentPersonal to locally stored data, or request StudentPersonal objects
from the zone by RefId. Objects often carry an attribute that identifies a particular object instance; this attribute is named RefId.
It is imperative that RefIds not clash with any other RefId. This is especially relevant when an agent manages a database comprised of a mix of objects;
for example, a library database containing patrons, which are a mix of both students and staff. To virtually eliminate the possiblity of duplicate object
identifiers and to provide a consistent, decentralized way of generating these identifiers, SIF
requires the use of a globally unique identifier (GUID) that MUST be generated per published algorithms
[RFC 4122] whenever a RefId is used.
GUIDs in SIF have their own format; they MUST be 32 characters long and contain only valid upper-case hexadecimal
characters (0-9, A-F) with no spaces or punctuation.
Object identifiers do not have to appear on any customer screens and they do not replace any identifiers currently in use by applications. Applications and application users users can still reference data as they always have. The GUID provides an additional key, which becomes the SIF primary key that agents use to reference an object within SIF.
As stated, object identifiers are also used to represent telationships between objects. Where referenced, RefId is typically prefixed
with the object name, e.g. StudentPersonalRefId in StudentPicture refers to the RefId of the StudentPersonal object corresponding
to the student photographed. Other more complex conventions surrounding object identifiers and RefIds can be found in Data Model.
When used as identifiers for objects that persist over time—take for instance the StudentPersonal object that
represents a student in a Zone—it is SIF's intent that object identifiers not change over time. The RefId attribute
for John Doe in first grade should have the same value when John Doe is in second grade, in middle school or in high school. This
persistence of object identifiers enables longitudinal tracking of data within SIF, especially where there exist no locally
unique identifiers associated with objects. Implementations SHOULD avoid reassignment
of object identifiers within a zone and as the primary home for individual objects may move from one zone to zone over
time (e.g. a student moving from a middle-school to a high-school zone).
Each application that wants to be a SIF application, or SIF-enabled application, must have an agent written for it. An agent is an extension to the application that communicates with the ZIS. An agent can be an integral part of an application itself, or may be a separate, specialized client of or interface to an application.
All applications that are part of a SIF zone must be
able to gracefully handle all SIF messages including those messages and data
objects that the application does not support.
It is RECOMMENDED that the application return an error SIF_Ack message to the ZIS for those messages
that the agent does not support (error category Generic Message Handling, error code "Message not supported").
An agent MAY return an "Immediate" SIF_Ack to the ZIS and ignore unsupported messages.
High-level functional requirements for all SIF-enabled applications include the following. More detail on particular requirements may be found in Messaging and Infrastructure.
Support for SIF HTTPS is REQUIRED of all agents. An agent MUST be able to communicate with the ZIS using SIF HTTPS, but it may attempt to communicate with the ZIS using any communication protocol defined in this or other specifications. SIF HTTP is the other communication protocol defined in this specification at this time. Support for any communication protocol other than SIF HTTPS is implementation-dependent. If connection attempts in protocols other than SIF HTTPS fail, a connection over SIF HTTPS should be made in order for communication to proceed. Given the sensitive nature of much of the data within the zone, it is RECOMMENDED that all communication occur over SIF HTTPS or similarly secure communication protocols.
Given a communication channel between agent and ZIS, an agent is REQUIRED to register with the ZIS
if it is not already registered or if it wishes to change or retransmit its registration settings.
The SIF_Register message provides the ZIS information regarding agent capabilities and requirements,
and allows the ZIS to contact the agent in the future if the agent is capable of accepting ZIS-initiated communications (a Push-Mode Agent).
An agent MAY also indicate its support for various data objects and associated messages using one or more
of the SIF_Provision, SIF_Provide and SIF_Subscribe messages.
When an application makes changes to its data that
correspond to a SIF object it supports, the application MUST be able to publish SIF_Events reflecting those data changes.
If the application/agent makes changes to its data in processing a SIF_Event it has received, it MUST NOT
publish an event that duplicates the changes as described in the processed SIF_Event.
Should the application/agent, however, make additional changes beyond those in the SIF_Event being processed,
the application SHOULD generate a new event describing the additional changes.
If an application does not support an optional field of an object or that element was not changed during the last edit, it MUST NOT send an empty element, (i.e., <BirthDate/> or <BirthDate></BirthDate> ); it MUST omit the element from the XML stream instead.
When publishing Add events, Agents MUST include
all elements listed as mandatory in Data Model for the object.
All agents MUST be prepared to handle SIF_Request messages for all objects gracefully. In the case where an agent
receives a SIF_Request for an object that it does not support, in addition to acknowledging the
receipt of the message to the ZIS it MUST send a SIF_Response message to the Requester with the SIF_Error element populated to indicate
the nature of the error (invalid object), a SIF_PacketNumber of 1 and the SIF_MorePackets element set to indicate that no further packets
will be sent in response to the SIF_Request.
If an application agent is a responder for any object, the agent must be prepared to process SIF_Request messages for that object.
This involves the ability of the agent to traverse the application database and construct an XML response stream based upon the parameters of the query request.
All responders MUST support SIF_Query and query conditions that reference root attributes of the object as well as any mandatory
elements within the object, along with their mandatory attributes. Responders SHOULD support query conditions
that reference optional elements and their attributes, when the application supports such queries. Responders MAY
support SIF_ExtendedQuery and MUST register their support for SIF_ExtendedQuery
using SIF_Provision and/or SIF_Provide.
When an agent is creating SIF_Response packets, it MUST attempt to ensure that each packet is no larger than the
SIF_MaxBufferSize specified by the SIF_Request. If for any packet a single packet does fit within the supplied SIF_MaxBufferSize, the agent
MUST,
in addition to acknowledging receipt of the message to the ZIS, send a SIF_Response message to the Requester with the SIF_Error element populated to indicate
the nature of the error, and the SIF_MorePackets element set to indicate that no further packets
will be sent in response to the SIF_Request.
The SIF_Request message also contains SIF_Version elements that specify which SIF versions the responding agent should use when preparing the response packets.
If a responding agent can support a single requested SIF version, it returns a response packet using that version. If more than one version is specified
and the responding agent supports more than one of those versions it SHOULD respond with the highest version it supports.
If the agent cannot support any requested SIF version, in addition to acknowledging receipt of the message to the ZIS, the agent MUST
send a SIF_Response message to the Requester with the SIF_Error element populated to indicate the nature of the error, a SIF_PacketNumber of 1 and the
SIF_MorePackets element set to indicate that no further packets will be sent in response to the SIF_Request.
If any other error occurs while creating SIF_Response packets for a given request, in addition to acknowledging receipt of the message to the ZIS,
the agent MUST send a SIF_Response message to the Requester with the SIF_Error element populated to indicate the nature of the
error, with SIF_MorePackets set to indicate that no further packets will be sent in response to the SIF_Request.
Agents supporting SIF_Requests MUST be able to return all of the object fields that the responding application supports or a
subset of the fields as
specified by the query request. For example, an Agent may request that only a student's graduation year be returned and not the entire StudentPersonal object.
If the responder does not support a requested element, it MUST NOT exclude the object from the response stream. Any
requested element that is unsupported is omitted from the response stream; when processing SIF_Query requests, parent elements of requested elements,
including the object itself, are included in the response stream.
If an application does not support an optional element of an object, it MUST NOT return an empty element. The element MUST instead be omitted from the XML stream.
Depending upon the type of architecture, the core application may need to be altered to ensure that the agent is able to forward changes to objects of interest to SIF. For example, an application that edits student data may need to be modified to capture the adds, changes, and deletes made to students and store them into a temporary repository until the agent can forward them to the ZIS. Other architectures provide the ability to trap these changes at a server level eliminating the need for any changes to the application itself.
To meet the SIF requirement of data robustness, it is highly RECOMMENDED that all changes to objects of interest to SIF be persisted using a database table, local message queue, or other highly reliable storage system. This specification allows for the ZIS and any or all agents to be offline at any given time. Without storing agent changes locally, these changes can be lost when the ZIS is temporarily unavailable; local storage allows these changes to be transmitted to the ZIS when it becomes available.
When an object is shared for the first time in SIF, it is the responsibility of the application making the object available to
assign its object identifiers/primary keys, typically a RefId in the form of a GUID, before releasing that object to the zone in an Add event or in
a SIF_Response. Some application databases are extended to include SIF object identifiers, others maintain
mappings from SIF object identifiers to locally-defined keys.
If an application changes data that maps to a SIF object, it is RECOMMENDED that only the changed fields be sent to the zone. This will result in smaller message sizes and improved performance.
To avoid unintentional overwriting of data, unsupported fields or fields that have not been changed MUST NOT be sent to the zone using empty XML elements, (i.e. <Name Type="04"/> or <Name Type="04"></Name> ); the fields MUST be omitted from the XML stream instead.
Supporting authentication is not a requirement but it is highly RECOMMENDED to ensure that your agent will be able to communicate with any ZIS. SIF does not mandate the use of authentication, but it is feasible that many SIF implementations will require this functionality. This is especially true for installations that may use the Internet to transport data.
Typically the authentication and verification mechanisms that are built into the network operating system or transport protocol can be leveraged. If these services are available, authentication and verification take place completely within the underlying security package.
The SIF HTTPS protocol supports authentication between an agent and a ZIS. If authentication is enabled and properly configured, a message receiver (agent or ZIS) can trust the SIF HTTPS implementation to verify that the message in its entirety comes from the claimed sender.
An Agent can be developed with a local queuing mechanism so that it can automatically cache incoming messages in a local queue and
can acknowledge receipt of each message to the ZIS with "Immediate" SIF_Ack messages
(which causes the ZIS to remove received messages from the agent's queue).
Agents with an Agent Local Queue do not need to send any "Intermediate" SIF_Acks to the ZIS.
Use of an Agent Local Queue can be used
to locally support selective processing of messages, similar to the functionality provided by Selective Message Blocking; its use
also allows more flexibility and robustness during application/system failure when successfully acknowledging events, requests and/or responses
before performing the corresponding SIF_Event, SIF_Request and/or SIF_Response handling.
Agent Local Queue is not a required feature of any Agent. Agent developers can choose not to develop the Agent Local Queue mechanism since this is not part of the compliance requirements for the specification at this time.
It is possible for a SIF Zone to contain Agents written to different versions of the SIF Implementation Specification
if a ZIS supports multiple versions in a Zone and has at least one version in common with all registered Agents.
As such, it is possible for a SIF Zone to contain Agents that have no versions in common with other Agents.
These Agents consequently have no ability to exchange SIF_Event, SIF_Request or
SIF_Response messages, unless the ZIS provides message conversion as described in
"Multiple Version" Zones.
As message conversion is an implementation-dependent feature of a ZIS, it is RECOMMENDED that Agents register in Zones and request data using SIF_Version wildcards
(see SIF_Register for format) that allow for the exchange of data
between Agents supporting any subset of releases within a major release cycle of this specification (e.g. 2.* or *
to accept any SIF_Message in the 2.x lifecycle). (Note that * allows messages from
any major version to be delivered, which can be structurally quite different across major versions and pose
development challenges, and is not particularly recommended for indicating the ability to receive messages
from all versions within a major version release cycle.) This maximizes the ability of Agents to exchange messages and data in these Zones
and, for customers, maximizes the utility of Zones supporting different versions of this specification.
Wildcard version support is particularly important for SIF-enabled applications that are not updated with each release of this specification. Furthermore, given that releases of the SIF Implementation Specification are on a more rapid release cycle beginning with version 2.1, typically smaller in scope than SIF Implementation Specification releases historically, it is anticipated that it will become more common for SIF-enabled applications in Zones to support different specification versions, and for more applications not to be updated with each release of this specification. Wildcard version support also allows applications to be SIF-enabled at any time in a SIF Implementation Specification major release cycle without risking the need to upgrade with the introduction of a new minor release of the specification, particularly when the new functionality offered by the specification does not apply to or impact the application.
Ignoring revision releases, the changes typical of releases within a given major version are limited to new data objects and optional additions to existing data objects (and optional infrastructure additions). This nature of a lower release being a subset of each higher release within a major release lifecycle—and of a higher release being a superset of each lower version—allows SIF-enabled applications access to the same elements they rely on at the time of their implementation from SIF messages defined by a number of SIF Implementation Specification versions. For associated implementation notes, see Wildcard Version Support Implementation Notes.
While wildcard version support in this specification is only RECOMMENDED, SIF-enabled application developers should be aware that this support may be mandatory in some SIF Certification Program product standards [SIFCertification] associated with a major release cycle, if application vendors wish to establish their applications as SIF Certified™.
The Zone Integration Server is the central integration point for all the agents in a zone. Depending on the message type, a ZIS either saves information in the messages that it receives or forwards the messages to other appropriate agents.
The ZIS implementer is free to internally manage registration and access permissions information in any form that the implementer supports. In order to provide an example of how an administration system may be structured, this document describes a database consisting of an Access Control List and Zone Status.
A ZIS MAY maintain access control on whether a zone administrator has granted an agent permissions to register.
A ZIS MAY exhibit behavior with regard to the ACL that could be perceived by an Agent as if virtual tables exists defining the following information:
| Field | Comments |
| Agent ID | The unique ID for an Agent (provided as the Source ID in a SIF_Register message) |
| Register | May this agent register in the zone? |
An example of this virtual table, which defines which agents are allowed to register in the zone, might be as follows:
| Agent ID | Register |
| RamseySIS | true |
In addition, a ZIS MUST exhibit behavior with regard to the ACL that could be perceived by an Agent as maintaining per-context/per-object permissions for each message associated with SIF's Publish/Subscribe and Request/Response models. When an agent tries to inquire about a student's personal information, for example, the ZIS needs to check if the agent has the proper permission to request such information. Access control is needed to ensure that the information available in SIF only originates from and is accessible by authorized agents.
| Field | Comments |
| Agent ID | The unique ID for an Agent (provided as the Source ID in a SIF_Register message) |
| Context Name | The name of the SIF Context to which the permissions apply |
| Object Name | The object being manipulated (e.g., StudentPersonal, etc.) |
| Provide | May this Agent register as the provider for this object in this context? |
| Subscribe | May this Agent register as a subscriber for this object in this context? |
| Publish "Add" Event | May this Agent publish "Add" events for this object in this context? |
| Publish "Update" Event | May the Agent publish "Update" events for this object in this context? |
| Publish "Delete" Event | May the Agent publish "Delete" events for this object in this context? |
| Request | May this Agent request this object in this context? |
| Respond | May this Agent respond to a request for this object in this context? |
It is important to understand that this is a virtual table, defining the appearance of the functionality to the Agents, the actual implementation of this functionality is at the discretion of the implementers of a ZIS. An example follows:
| Agent ID | Context Name | Object Name | Provide | Subscribe | Publish "Add" Event | Publish "Update" Event | Publish "Delete" Event | Request | Respond |
| RamseySIS | SIF_Default | StudentPersonal | true | true | true | true | true | false | true |
| RamseySIS | SIF_Default | LibraryPatronStatus | false | false | false | false | false | true | false |
| … | … | … | … | … | … | … | … | … | … |
In addition to access control permission violations, attempts to register any of this functionality with the ZIS may fail due to other reasons; e.g. unsupported transport mechanisms, there already being a provider for an object, etc. As a result, an Agent SHOULD be able to gracefully handle corresponding error conditions or report those errors to a zone administrator.
The ZIS MUST maintain the status of the zone for implementation purposes, as well as for
communicating this status to other agents, as defined in SIF_ZoneStatus, when requested.
This status includes but is not limited to:
Providing examples of virtual tables that illustrate storage of all the information associated with SIF_ZoneStatus is beyond the scope of the specification;
implementers should refer to SIF_ZoneStatus for requirements.
Zone Integration Servers MUST maintain a registry of the contexts used in each zone in order to perform contextual message routing
and to populate the SIF_ZoneStatus/SIF_Contexts element.
This registry will always contain, at a minimum, the official list of contexts defined by the version of SIF that the ZIS supports.
Beginning with SIF 2.0, that means that each zone will, at a minimum, support the SIF_Default context.
A ZIS MAY support allowing additional contexts to be defined within the context registry at the discretion of the ZIS administrator.
Access Control Lists within each context MUST also be able to be managed by the ZIS administrator.
The set of permissions for each agent within each context MUST be able to be set differently than ACL permissions within a different context for the same agent.
An agent can obtain a list of all contexts currently defined in a zone by requesting the SIF_ZoneStatus object and enumerating the children of its SIF_Contexts element.
An agent can determine its ACL permissions within the zone and each context by referring to the SIF_AgentACL object and enumerating the
permissions and contexts defined within it.
A ZIS MUST provide an interface for Zone Administrators to configure zone settings, including access control permissions. Given the distributed nature of SIF, it is RECOMMENDED this be a Web-based interface. Some of the areas that require administration are:
SIF_EncryptionLevel for the zone (if only one encryption level is supported, configuration options are unnecessary).SIF_AuthenticationLevel for the zone (if only one authentication level is supported, configuration options are unnecessary).SIF_MaxBufferSize for the zone.
Selective Message Blocking is a feature that MUST be implemented by a ZIS to enable
non-multitasking agents unable to persist portions of their message queue locally
to request information from other Agents while processing a SIF_Event message,
without causing communication "deadlock" between an agent and a ZIS.
This feature allows an agent to inform the ZIS with an "Intermediate" SIF_Ack message that the ZIS must
temporarily stop delivering SIF_Event messages to the agent. The
"Intermediate" SIF_Ack message must not be used by agents in response
to messages other than SIF_Event. The ZIS, however, can deliver other agent-destined messages, SIF_Request and SIF_Response, to this agent.
After it finishes processing the SIF_Event message this agent sends the "Final" SIF_Ack message to the ZIS,
which will discard the blocked SIF_Event message and resume normal delivery of all messages, including SIF_Events. SMB is supported for both
Push and Pull modes.
SIF_Event message to an agent, the ZIS receives an Intermediate SIF_Ack (SIF_Status/SIF_Code=2) from the agent,
the event is blocked and all SIF_Event messages destined for the agent, whether already in the queue or that arrive while blocked, are considered frozen.
The ZIS will not deliver any SIF_Event messages that are frozen.SIF_Ack at all is received, or if a transport error occurs, this SIF_Event must be considered an undelivered message.
The next message to be delivered to the agent will be this event.SIF_Event message to the agent until a "Final" SIF_Ack is received (SIF_Status/SIF_Code=3),
giving the ZIS permission to discard the original event and resume event delivery.
The SIF_OriginalMsgId in the "Final" SIF_Ack MUST contain the SIF_MsgId of the blocked SIF_Event.SIF_Events are frozen, the next message to be delivered is the oldest message that is not a SIF_Event message.
Once SIF_Events are unfrozen, all remaining messages in this agent's queue, including SIF_Events,
will be delivered in the order in which they have been received by the ZIS.SIF_Wakeup or SIF_Register message then the block on any frozen SIF_Event messages
will be removed and the originally blocked message will be the next message delivered to the Agent.For a detailed example of SMB, see the Selective Message Blocking (SMB) Example.
To ensure interoperability, SIF defines a set of messages that are exchanged between agents and Zone Integration Servers. The SIF messages are used to perform various operations such as provision, subscription, event reporting, request and response, and ZIS administration.
SIF recommends that each message receiver validate any incoming message to ensure that it is a valid SIF message. A message receiver should discard any messages that do not conform to the definition of SIF_Message and return an error to the originator of the message.
This specification will evolve over time to include new messages and modifications to messages that have been defined. Each agent and ZIS should explicitly define which version(s) of the specification they support and validate each incoming message according to its version.
The SIF Association provides an XML Schema [SCHEMA] corresponding to this version of the specification for ZIS and agent implementations that choose to perform optional message validation. Implementations are free to include additional validation above and beyond the validation capabilities that XML Schema provides.
The schemas for all versions of this specification are available from the SIF Association and can be referenced by ZIS and
agent implementations that choose to perform optional message validation.
This allows implementations to choose schemas based on the particular version in
use by an agent or a ZIS. SIF messages MUST NOT be transmitted with hard-coded references to
DTDs, schemas or other validation mechanisms. The XML "doctypedecl" (<!DOCTYPE SIF_Message… ) MUST NOT occur in SIF XML messages,
nor should xsi:schemaLocation be used on SIF_Message.
The schemas for supported versions of the SIF Implementation Specification enforce ordering of elements and data typing within objects, as per the element tables given in Infrastructure and Data Model. In the event that ZIS and agent implementations choose not to perform message validation, ZIS and agent implementations must still send elements as ordered with the types specified in the element tables (i.e., well-formed AND valid XML must be sent for approved objects even if validation is known to be turned off). When XML validation is turned off, the sending of draft and locally-defined objects not included in the schemas becomes possible, and these objects may experimentally be sent as desired until they make their way into future versions of the specification and supporting schemas.
ZIS implementations are in the unique position of not only sending messages they themselves formulate; they also forward messages received from agents. When optional message validation is not being performed by a ZIS, it is possible that the ZIS may receive a well-formed but invalid XML message from a non-compliant agent. Under these circumstances, and being the routing mechanism it is, a ZIS is under no obligation to correct an invalid XML message it receives from an agent for delivery to other agents. Zone administrators can prevent invalid XML messages from being delivered if the ZIS supports message validation and they choose to turn that feature on, if configurable. Should it receive an invalid but well-formed message from an agent, a ZIS not performing message validation delivers the message like any other to destination agents.
Each message originating from an agent or ZIS needs to
have a message identifier (SIF_MsgId) that is used to identify the
message. In order to eliminate the possibility of duplicated message
identifiers, and to provide a consistent way of generating these identifiers,
SIF requires the use of a globally unique identifier [RFC 4122] as message identifiers.
The reason that a unique identifier is required is that many messages are handled asynchronously in SIF.
This means, for example, that SIF_Responses for a given SIF_Request message may not arrive until some time in the future.
When the SIF_Response arrives, it will contain the original SIF_MsgId but no other information about the original message is guaranteed to be provided.
The message originator must ensure that it will be able to match up the SIF_Response with the original message based solely on the message identifier.
For further information concerning the generation of GUIDs, see [RFC 4122].
Because of policy or legislation, providers of extremely sensitive data must never expose that data over an insecure channel. An insecure channel at delivery time is one whose levels of authentication (SIF_AuthenticationLevel) and data encryption (SIF_EncryptionLevel) fall below the values specified by the originating sender. Once the data is communicated to the ZIS, the originator of the message depends upon the ZIS to enforce the security levels requested and the ZIS must not deliver that message to recipient agents using an insecure channel. The originating agent requests the use of a secure channel at delivery time by incorporating a SIF_Security element in the header of the message. The SIF_Security element contains SIF_AuthenticationLevel and SIF_EncryptionLevel elements that define the minimum level of security a data transport channel must provide upon delivery. If a ZIS does not deliver a message due to insufficient security of the connection with a recipient agent, it is recommended that the ZIS log the inability to deliver the message due to security requirements.
The only SIF messages that currently originate with an agent and that are ultimately delivered to other agents are SIF_Request, SIF_Response and SIF_Event. An originating agent may add a SIF_Security element to all messages, but these three messages are the only ones where SIF_Security will be examined and processed by the ZIS. SIF_Security is used by an originating agent to specify the security requirements of the communication channel between the ZIS and any recipient agent at delivery time. The semantics of including the SIF_Security element on messages other than SIF_Request, SIF_Response and SIF_Event are reserved for future versions of the specification.
The specification provides several levels of authentication and encryption protection.
The CN field is more commonly known as the "Common Name" field. SIF_AuthenticationLevel 3 requires that the CN contents match the host where the message was originated. For instance, a CN entry could be "sifinfo.org" or perhaps "207.95.37.30". If a ZIS at SifInfo.org (IP address 207.95.37.30) contacts an agent at MyAgent.sifinfo.org, the agent's SIF HTTPS transport layer can look at the CN entry in the certificate that was presented by the ZIS and compare it to the actual IP address of the ZIS. SIF_AuthenticationLevel 3 ensures that not only a valid and trusted certificate was presented but that the agent is actually communicating to the ZIS located at the IP address referenced in the certificate.
Because security is a cornerstone of the SIF specification, it is recommended that all ZIS and Agent implementations support client authentication as well as server authentication. When client authentication is being used, the connection first authenticates the server (the party that is being contacted) and if the authentication was successful, the server will request that the client present its certificate for authentication. In this manner, both the ZIS and the agent confirm that they are communicating with the proper parties.
Since client authentication is not universally available in all SIF HTTPS implementations, client authentication is only recommended. The need for client authentication is reduced somewhat by using asynchronous message delivery (Push mode) since the ZIS and the agent are both server type applications and will authenticate each other. The need for client authentication is greater for those agents polling for messages (Pull mode) because the ZIS never has to initiate contact with the agent.
If a SIF_Request, SIF_Response or SIF_Event is received by the ZIS that does not contain a SIF_Security element,
the ZIS assigns the lowest level (0) to both the SIF_AuthenticationLevel and SIF_EncryptionLevel requirements for the message, unless
a Zone administrator has configured higher minimum encryption and authentication levels for the Zone.
This means that the ZIS may distribute this message to any agent that has registered with the ZIS subject to the access control security provisions in place for the zone.
The lack of a SIF_Security element does not mean that the message will be transported in an insecure manner. Recipient agents communicating with the ZIS over secure channels will receive the message in a secure manner, consistent with the connection. Omitting the SIF_Security element simply allows for those agents that communicate over insecure channels to receive the message, should a zone allow for insecure channels. A zone administrator can prevent messages without SIF_Security elements being communicated over insecure channels by configuring the ZIS and agents in the zone such that a minimum security level is maintained, below which communication is impossible.
For ZIS and agent implementations that support communication protocols or transport implementations where the security of a channel cannot be determined at delivery time, it is recommended that the zone administrator configure the ZIS and agents in the zone such that a minimum security level is maintained, below which insecure connections cannot be established.
If authentication based on certificates is being used, care needs to be given to determine if Level 2 (anonymous certificates) will provide the necessary level of protection. With Level 2 authentication, it is possible to use a web browser to make secure connections to the ZIS using the certificates that are built into the browser. This level of authentication is what is used by almost all Internet transactions (stock trading, shopping, financial, etc.). Level 2 does expose the user to a risk of a "man-in-the-middle" attack that can't occur using Level 3 authentication.
Level 3 mandates that a certificate issued by a trusted authority, (i.e. school district), be installed in the web browser before the browser will be able to connect to the ZIS. This may place unnecessary burdens on the client especially if it is likely that authorized users may wish to connect to the ZIS using a variety of browsers.
Weaknesses in a cipher algorithm aside, the major governing factor as to the strength of data encryption is the length of the cipher key. Thus a 128-bit implementation typically provides stronger encryption than an 80-bit implementation. Please note that support of some SIF encryption levels may be subject to export control, limiting distribution of all levels in all countries [EXPORT].
There are also two main types of cipher algorithms. The first is called a symmetric cipher, which uses the same key to encrypt and decrypt the data. The second type is called public-key cipher, which depends upon using a private key of the sender along with the public key of the receiver. Because of the nature of public-key ciphers, a larger number of bits must be used to achieve a comparable level of encryption strength.
The SIF_EncryptionLevel bit sizes are based on symmetric ciphers. A table that lists the equivalent key length for a public-key cipher is listed below.
| Symmetric Key Length | Public Key Length | Strength |
| 40 bits | 256 bits | Very weak, not recommended except for very minimal protection (i.e. prevents casual snooping but can be broken in minutes by knowledgeable attackers). |
| 64 bits | 512 bits | Weak. The current U.S. "standard" has been bumped up to 64 bits from 56 bits but the key length is still weak for sensitive data. |
| 80 bits | 768 bits | Moderate |
| 128 bits | 2048 bits | Strong, recommended for Internet |
For more information regarding this topic, please refer to Chapter 7 of [Schneier].
It is important for SIF to guarantee message delivery no matter what happens during delivery of a message,
including an unexpected network breakdown or system crash.
This requires that each agent and ZIS save each message in permanent storage.
At delivery time it is also possible, however, for a ZIS to be prohibited from delivering a message due to security requirements
requested by originating agents for individual messages.
If this occurs, it is recommended that ZIS implementations discard the affected message so that delivery of other messages may proceed.
If the ZIS does discard the message, the ZIS MUST report a SIF_LogEntry event with the appropriate error category and code,
containing a copy of the SIF_Header from the original message.
In addition, it is recommended that the ZIS log the delivery failure to its own log.
When a message is delivered under normal circumstances by a ZIS, an agent will return an "Immediate" SIF_Ack or a SIF_Ack with any applicable error condition, signaling the ZIS that it may delete the message from permanent storage. In the case of events, agents may also return an "Intermediate" SIF_Ack to invoke Selective Message Blocking (SMB). In that case, the ZIS will not delete the current SIF_Event from permanent storage until the agent sends a "Final" SIF_Ack to the ZIS.
When a message is sent to the ZIS under normal circumstances by an agent, the ZIS returns a successful SIF_Ack or a SIF_Ack with any applicable error condition to indicate to the agent that it has in fact received the message and that the agent may delete the message from any permanent storage.
If a ZIS or agent encounters a transport error in sending a message, it is recommended that the sender retry sending the message. Transport errors where retrying the message is warranted include, but are not limited to, a connection close without a SIF_Ack returned, a transport error or a SIF_Ack with an error category of 10 indicating a connection cannot currently be established, etc. A ZIS in particular must retry delivery of messages from the agent queue until a SIF_Ack that removes the message from the agent's queue is received, subject to certain undeliverable error conditions (e.g. security requirements cannot be negotiated, maximum buffer size too small, etc.). Facing such error conditions, other potentially unresolvable transport errors, or if a SIF_Ack is returned with any other type of error category, the sender may decide not to retry or—when queued, to delete—a message to avoid a potential deadlock condition. Agents returning SIF_Ack messages with error conditions should be aware that such acknowledgements will remove the currently pending message from their delivery queue.
All SIF messages follow the same model. The sender posts a message and receives a SIF_Ack back as a response. The posting of the message by the sender and the receipt of the SIF_Ack from the receiver constitutes one complete cycle. Agents and ZISes can function as senders or receivers, depending on the type of message. The message process is identical, regardless of the type of message being sent.
If for any reason a sender inadvertently resends a message
with a given SIF_MsgId and the receiver detects this, the receiver may return a
SIF_Status code indicating that it already has the message. This
SIF_Status code is considered a success; the receiver simply discards the
duplicate message and continues handling of the original message.
There are two models for delivering messages to an agent, "Push" and "Pull." An agent specifies which mode it wants to use when it registers with the ZIS.
"Push" refers to the action by a ZIS to actively deliver messages to an agent without the agent having to initiate contact with the ZIS. When the ZIS receives a message for an agent and the agent is not in "Sleep" mode; the ZIS will initiate contact with the agent and send the message to the agent.
"Pull" refers to the action by an agent to explicitly request a single message from the ZIS. When an agent is ready to receive a message, it sends a "Pull" request to the ZIS, to obtain a message that the ZIS has saved in the queue for the agent. After receiving the pull request, the ZIS will examine the agent's queue and either returns a message or a status code indicating that no messages are available for the agent.
Both modes serve useful purposes. The key requirement is that both an agent and its ZIS must communicate using the SAME mode to avoid potential conflicts.
At delivery time, be it in push or pull mode, a ZIS may encounter messages that it is prohibited from delivering,
e.g. due to security requirements requested by originating agents for individual messages, etc.
If this occurs, it is recommended that ZIS implementations discard the affected message(s) so that delivery of other messages may proceed.
If the ZIS does discard a message, the ZIS MUST report a SIF_LogEntry event with the appropriate error category and code,
containing a copy of the SIF_Header from the original message.
SIF_LogEntry/SIF_Desc must contain the SourceId of the agent that has failed to receive the message.
In addition, it is recommended that the ZIS log the delivery failure to its own log.
When an agent has registered using the "Push" mode, the agent assumes that the ZIS will open a transport connection and send the next available message to the agent. An agent can reply to the sent message with an "Immediate" or optionally—in the case of SIF_Events—an "Intermediate" SIF_Ack, invoking Selective Message Blocking (SMB); it can also reply using a SIF_Ack with any applicable error condition. "Immediate" or error SIF_Acks remove the current message from the agent's queue, freeing any remaining or future messages to be delivered to the agent. A "Final" SIF_Ack sent to the ZIS will terminate SMB, removing the frozen event from the agent's queue, freeing any remaining or future messages to be delivered to the agent.
When an agent has registered using the "Pull" mode, the agent requests a message from the ZIS by sending a SIF_GetMessage message to the ZIS.
An agent can only issue a SIF_GetMessage to request a message if the agent has previously sent a successful SIF_Register message specifying Pull mode. If the ZIS receives a SIF_GetMessage request and the agent hasn't registered using the Pull mode, the ZIS must return a SIF_Ack containing an error category of Registration and an error code indicating that the agent has registered using Push mode.
After receiving a SIF_GetMessage request from an agent, the ZIS will return the next message available for delivery to the agent,
subject to Selective Message Blocking. The criteria used to select the message are identical to that used if the ZIS were to Push a message to an agent.
If a message is available for the agent, the ZIS will return a SIF_Ack message with a SIF_Status/SIF_Code of 0 and SIF_Status/SIF_Data containing the message from the queue:
When a pull-mode agent supports multiple SIF specification versions, the version of the SIF_Ack message returned by the ZIS must match the version of any SIF_Message contained in SIF_Status/SIF_Data. For example, if an agent supports versions 1.1 and 1.5 (or 1.*) and the next message in the agent's queue has a SIF_Message/@Version value of 1.5, the Version attribute of the SIF_Ack message returned by the ZIS must be 1.5, even if the pull-mode agent sent its SIF_GetMessage in a 1.1 SIF_Message. For an agent that supports both 1.1 or later versions and pre-1.1 version(s) (e.g. 1.0r2), when the next message in the agent's queue is from a pre-1.1 agent, the ZIS must return the message in a SIF_Ack message as defined by the pre-1.1 specification.
A pull-mode agent removes the returned message from its queue in one of three ways. In each case the value for the SIF_OriginalMsgId element in any SIF_Ack(s) created by the agent originates from the SIF_MsgId of the SIF_Message returned as SIF_Data by the ZIS. Typically a pull-mode agent removes the message from its queue by sending an "Immediate" SIF_Ack to the ZIS; an agent may also send a SIF_Ack with any applicable error condition to the ZIS. The ZIS then removes the message from the agent's queue and returns a successful SIF_Ack. If the message is a SIF_Event and the agent wishes to invoke SMB, it can instead notify the ZIS that it is processing the event by sending an "Intermediate" SIF_Ack (which the ZIS acknowledges with a successful SIF_Ack) and later sending a "Final" SIF_Ack when the SIF_Event processing is complete. When the ZIS receives the "Final" SIF_Ack, it removes the SIF_Event from the agent's queue and returns a successful SIF_Ack.
If there are no messages in the agent's queue that can be delivered, the ZIS will return a SIF_Ack message with a SIF_Status/SIF_Code of 9 to indicate that there are no messages available for the agent:
It is possible for a zone to contain agents written to different versions of the SIF Implementation Specification if a ZIS supports multiple versions in a zone and has at least one version in common with all registered agents. It is possible that two agents in the same zone—both successfully registered—have no version in common, and this affects message delivery by the ZIS in the following manner.
When the next message to be delivered to a given agent has a SIF_Message/@Version attribute that the agent is known not to support,
the ZIS cannot successfully deliver that message to the agent without conversion.
Should a ZIS implementation choose to convert messages on the fly as a "value-add" feature, it is free to do so;
this specification does not prescribe how to convert messages, and support for such conversion is implementation-dependent.
However, if the ZIS does not or cannot convert the message such that it can be delivered,
it should discard the pending message so that delivery of other messages may proceed.
If the ZIS does discard the message, the ZIS MUST report a SIF_LogEntry event with the appropriate error category and code,
containing a copy of the SIF_Header from the original message.
SIF_LogEntry/SIF_Desc must contain the SourceId of the agent that has failed to receive the message.
In addition, it is recommended that the ZIS log the delivery failure to its own log.
The Infrastructure messages are used by SIF to encapsulate and transfer the data objects. They form a messaging application program interface (API) which is expressed in XML.
It is a design objective to express the entire Infrastructure API in XML and not to have dependencies upon any underlying transport layer to provide functionality other than the transportation of the XML from client to server and back. This ensures that the Infrastructure messages can be carried over a variety of communication transports.
The infrastructure depends upon the transport layer to provide a reliable connection to move messages back and forth from client and server. The transport layer is also responsible for providing data security by means of data encryption and authentication of the client and server. Some transport layers even provide data compression, which is an important factor when processing a large volume of XML messages.
By delegating the authentication, compression, and encryption to the transport layer, it makes the user interface to the transport simpler. A client that wishes to send an infrastructure message assembles the message in XML and then hands it off to the transport layer for delivery. The transport layer takes the XML message and transfers it to the server where it is taken from the transport layer and processed.
In moving from the client to the server, the transport may have compressed, encrypted, and authenticated the connections but all of this is transparent to the users of the Infrastructure API. To the user, it is XML in and XML out.
Different types of transports are or will become available providing various features and benefits. An Agent or ZIS MAY employ multiple transport protocols but they MUST support SIF HTTPS.
Please note that throughout this specification transport layer errors are sometimes illustrated as SIF_Ack messages with SIF_Error/SIF_Category of Transport and applicable error codes. Under many transport error conditions, these SIF_Ack messages could not be returned or sent by the remote host. Depending on the SIF infrastructure transport layer implementation these messages may be generated by the implementation (e.g. when a connection to a server cannot be established), or may occur as transport layer errors or exceptions in the underlying network operating system or transport protocol. Both should be treated equivalently.
In order to ensure that Agents and Zone Integration Servers can communicate with each other regardless of vendor or platform, all Agent and ZIS implementations MUST support the SIF HTTPS transport layer protocol.
SIF HTTPS is a combination of the HTTP 1.1 protocol [RFC 2616] with secure socket layer (SSL) protocols, resulting in an easy-to-use and secure transport protocol. The RECOMMENDED SSL implementation is TLS 1.0 [RFC 2246]; however, SSL 3.0 [SSL3] is also supported and SSL 2.0 client hellos [SSL2] used to negotiate TLS 1.0 or SSL 3.0 connections are also permitted. Support for the SSL 2.0 protocol itself—aside from its client hello message—is not provided in SIF. Due to the age of the SSL 3.0 and SSL 2.0 protocols and the increasing prevalence of TLS 1.0, The SIF Association expects to deprecate support for the SSL 3.0 protocol and SSL 2.0 client hellos in future major releases of this specification.
Being based upon HTTP 1.1, the SIF HTTPS and SIF HTTP protocols support persistent or keep-alive connections that greatly increase the message throughput between sender and receiver. This is an especially important factor when using HTTP in conjunction with secure socket layers, where there is a significant amount of overhead when initially opening a connection.
When using HTTP 1.1 with SIF, [RFC 2616] can be used as a reference, however SIF uses a subset of the HTTP 1.1 protocol. For example, only the POST method and the 200-OK response notice are used by the SIF HTTPS protocol.
Support of Transfer Encoding and data chunking ([RFC 2616], Section 3.6) is not required for SIF HTTPS. An implementation of the protocol may support Transfer Encoding and data chunking but it must be able to communicate successfully with a client or server that does not support this feature.
Because protocol changes are handled at the Infrastructure
XML API level, a client or server must not use the Connection:
Upgrade or Upgrade: xxx headers to invoke a request for a
protocol change. If a client or server receives an upgrade header, it must ignore that header and not change communication protocols.
A client is the party (Agent or ZIS) who initiates a connection to a remote machine. The remote end (ZIS or Push-Mode Agent) is known as the server.
A client using the SIF HTTPS protocol opens a connection to the server and sends a HTTP 1.1 POST request with the SIF Infrastructure XML message as the POST payload. The server responds with an HTTP response with the Infrastructure XML acknowledgement message as the response payload. Clients MUST encode the XML message using UTF-8; servers MUST be able to process UTF-8-encoded XML and SHOULD expect all incoming SIF XML messages to be encoded using UTF-8.
The default behavior for HTTP 1.1 is to use persistent or "keep-alive" connections. When operating in this mode, the client may send additional POST requests and receive the HTTP responses using the same connection. Clients SHOULD use persistent connections for performance reasons but MUST be able to use non-persistent connections if the server does not wish to use persistent connections.
The following HTTP request and common headers defined in [RFC 2616]MUST be present in all SIF HTTPS messages sent by a client:
| Header | Description | Required Contents |
| Content-Length | The exact size of the attached payload (XML message) | |
| Content-Type | Describes the contents of the request. Firewall and web server programs can filter messages going through a network by examining this header. | application/xml;charset="utf-8" |
| Host | Specifies the Internet host and port number of the destination server |
Note that all header values MUST conform to the requirements of [RFC 2616] and
MAY take equivalent forms subject to those requirements (e.g. application/xml;charset=utf-8 (no quotes),
application/xml; charset=utf-8 (optional spacing), etc.).
In addition to the headers above, a client may
include a Connection: close header in the HTTP request if it
wishes to close the current connection after receiving the response. If
this header is included, the client MUST NOT send additional requests on
this connection. The client MUST close the connection after receiving the response.
Clients may also include an "Expect: 100-continue" header (see below).
Additional headers beyond the required and optional headers listed here MAY be included by a client; however, the server MUST be able to successfully process POST requests that only contain the required headers.
Implementations of SIF HTTPS MUST be able to specify the value for the path (/MyPath in the example)
as the Agent or ZIS may require a specific value for routing purposes.
The following HTTP response and common headers defined in [RFC 2616] must be present in all SIF HTTPS responses messages sent by a server:
| Header | Description | Required Contents |
| Content-Length | The exact size of the attached payload (XML message) | |
| Content-Type | Describes the contents of the request. Firewall and web server programs can filter messages going through a network by examining this header. | application/xml;charset="utf-8" |
| Date | The current date and time in the format described in RFC 2616 Section 3.3. Note that the date is UTC based and NOT local time. | |
| Server | Identifies the server sending the response. Clients may use this information to infer information about the server being contacted (vendor, model, version, capabilities, etc.) |
Note that all header values MUST conform to the requirements of [RFC 2616] and
MAY take equivalent forms subject to those requirements (e.g. application/xml;charset=utf-8, application/xml; charset=utf-8, etc.).
In addition to the headers above, a server MAY
include a Connection: close header in the HTTP response if it
wishes to close the current connection after sending the response. The
server MUST close the connection after sending the response.
The server MAY include additional headers; however, the client MUST be able to successfully process response notices that only contain the required headers and optional header listed here.
Although the SIF HTTPS protocol uses the 200-OK response notice to communicate all responses, Agent or ZIS implementations could be built using existing web server infrastructures. As such, SIF HTTPS implementations should expect the possible receipt of other HTTP 1.1 response notices.
This response message status is generally returned if the
client has included an Expect: 100-continue header in its
request. Certain web server implementations return a 100 (Continue)
status response even though the original request did not contain an
Expect: 100-continue header. When a client receives an
unexpected response with a 100 (Continue) status, it must discard that response and wait for a subsequent final (e.g. 200-OK) response.
Clients explicitly requesting a 100 (Continue) status response by including an Expect: 100-continue header in a
request should proceed with the request body according to section 8.2.3 of the HTTP 1.1 [RFC 2616]
specification upon receipt of the 100 (Continue) status response.
A SIF HTTPS client may include an Expect: 100-continue header but generally does not.
If it does, however, servers (ZIS and push-mode agent implementations) must handle the header according to section 8.2.3 of the HTTP 1.1 [RFC 2616] specification, possibly returning an intermediate response with 100 (Continue) status, for communication to proceed correctly.
A server should only return 200-OK response notices but may return other notices. Servers built using existing web server technology are more likely to return other types of response notices. If a client receives any 3xx, 4xx, or 5xx response notices, it must treat these responses as if a transport error has occurred.
The SIF HTTP protocol is identical to the SIF HTTPS transport without a secure socket layer to provide data encryption and authentication.
An Agent or ZIS MAY implement the SIF HTTP transport but MUST implement the SIF HTTPS protocol.
Because of the sensitive data being exchanged in SIF, it is RECOMMENDED that only SIF HTTPS be used.
It is possible that compression can improve network throughput in SIF implementations where large amounts of data are transferred over SIF HTTP(S), either horizontally or vertically.
The HTTP 1.1 specification [RFC 2616] allows for negotiating the content encoding (and compression) of server responses using
the Accept-Encoding request header and the Content-Encoding response header. Registered content encodings include in
addition to the default uncompressed identity encoding a number of compressed encodings: gzip, compress
and deflate. A client can specify one or more encodings to use in a response along with its preference for each using Accept-Encoding,
and the
server responds accordingly, per the HTTP specification. If the server does not support a requested encoding, it is recommended the server return a
406 (Not Acceptable) status code.
The content encoding of any HTTP entity body, either in a request or a response, is indicated using the Content-Encoding header,
which is considered a modifier to the Content-Type header.
A client may compress or apply an encoding to the body of an HTTP request and indicate it has done so with an appropriate Content-Encoding
value. It is recommended that a server that cannot or will not accept a particular encoding return a 415 (Unsupported Media Type)
status code.
With these HTTP-defined headers, SIF Agents and Zone Integration Servers have the ability to compress or negotiate compression of SIF HTTP(S) request and response entity bodies using any version of SIF where the transport protocol is SIF HTTPS or SIF HTTP. However, to increase interoperability of Agents and Zone Integration Servers that wish to compress requests or receive compressed responses beyond the level of trial and error in an environment where server status codes are not guaranteed, the following mechanisms were developed in SIF Implementation Specification Version 2.1.
In both SIF_Register and SIF_ZoneStatus the following SIF_Property is defined when used in
conjunction with a SIF_Protocol/@Type value of HTTPS or HTTP:
SIF_Name
|
SIF_Value
|
|---|---|
Accept-Encoding
|
An Accept-Encoding header value as per HTTP 1.1 [RFC 2616]. |
This property indicates that an HTTP(S) server can accept corresponding content encodings with an appropriate Content-Encoding header value.
The recommended compression algorithm for use in SIF is gzip. It is NOT RECOMMENDED
that the identity (uncompressed) encoding ever be explicitly excluded in the Accept-Encoding SIF_Property.
A client (ZIS, Push- or Pull-Mode Agent) that wishes to receive a compressed response MUST include an Accept-Encoding header,
per HTTP 1.1, and MUST be prepared to handle a 406 (Not Acceptable) or other HTTP error, in which
case the client SHOULD assume compression using the specified algorithm(s) is not supported and retry communication as per SIF HTTPS Transport
or SIF HTTP Transport above. Clients MUST be prepared to receive identity-encoded
(unencoded) responses unless the client explicitly excludes identity in its Accept-Encoding header, which is NOT RECOMMENDED.
Zone Integration Servers MAY consult a Push-Mode
Agent's registered SIF_Protocol/SIF_Property value where SIF_Name is Accept-Encoding before contacting
the Agent and SHOULD assume that posting a corresponding encoded entity body accompanied by the applicable Content-Encoding
header value will be processed without content encoding support errors by the Agent.
Push- and Pull-Mode Agents MAY consult a Zone's supported compression algorithms in
the SIF_ZoneStatus/SIF_SupportedProtocols/SIF_Protocol/SIF_Property entitled Accept-Encoding in SIF_Name
before contacting the Zone Integration Server and SHOULD assume that posting a corresponding encoded entity body accompanied by the applicable Content-Encoding
header value will be processed without content encoding support errors by the ZIS.
A server (ZIS or Push-Mode Agent) that receives an HTTP request with an Accept-Encoding header MUST process the request
per HTTP 1.1's Accept-Encoding specification. It is RECOMMENDED that servers return a
406 (Not Acceptable) status when a requested encoding cannot be negotiated.
A server that receives an HTTP request with a Content-Encoding header specified MUST
process the request per HTTP 1.1's Content-Encoding specification. It is RECOMMENDED that
servers unable to process a particular content encoding return a 415 (Unsupported Media Type) status code.
A Push-Mode Agent that wishes to receive compressed/encoded requests from the ZIS MUST register its preference
with the ZIS in the SIF_Register/SIF_Protocol property entitled Accept-Encoding in SIF_Name, providing
an Accept-Encoding value in SIF_Value per HTTP 1.1 (the recommended compression algorithm for SIF is gzip).
The Agent
MUST be prepared to handle an error SIF_Ack from the ZIS when registering Accept-Encoding
(SIF_Error/SIF_Category of 5 [Registration], SIF_Error/SIF_Code value of 10) if the ZIS
cannot support at least one specified encoding
and SHOULD re-attempt registration without Accept-Encoding.
Upon successful registration of an Accept-Encoding value, the Agent SHOULD expect to receive
requests from the ZIS encoded accordingly, but it MAY received identity-encoded (unencoded)
requests unless identity was explicitly excluded in the registered Accept-Encoding value.
A Zone Integration Server that receives a SIF_Register/SIF_Protocol/SIF_Property named Accept-Encoding in SIF_Name
must fail the attempt to register if the ZIS does not support at least one of the specified encodings
(SIF_Error/SIF_Category of 5 [Registration], SIF_Error/SIF_Code value of 10). While this property is typically registered
by Push-Mode Agents, Pull-Mode Agents may also specify this property when registering. A ZIS SHOULD compress requests
when contacting a Push-Mode Agent if the Agent has previously registered that preference, but it MAY send uncompressed
requests if the Push-Mode Agent did not explicitly exclude the identity encoding in its registered Accept-Encoding value.
Zone Integration Servers that support handling of compressed/encoded requests SHOULD return an Accept-Encoding
header SIF_Value in the SIF_ZoneStatus/SIF_SupportedProtocols/SIF_Protocol/SIF_Property named Accept-Encoding in SIF_Name.