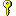In addition to SIF messages and strictly infrastructure-related objects like SIF_ZoneStatus, the Infrastructure
Working Group occasionally defines data model objects that either do not fall neatly within the purview of currently
existing data model working groups (e.g. the Authentication object) or that can be provided by the ZIS and agents
alike—typically metadata about a zone as opposed to data directly originating from the K-12 instructional and
administrative environment (e.g. SIF_LogEntry).
6.9.1 Authentication
The Authentication object allows a system that stores usernames and/or passwords to share them with other applications through SIF.
The provider of the Authentication object may only support providing a username or a password, or it may support both.
The Authentication object is also able to transmit a user's network identity through SIF.
If the user has an account in a network directory system that supports LDAP, the user's distinguishedName or username is shared
to uniquely identify the user to applications that support LDAP or native network authentication options.
Details of how to implement the password element are included below the object definition.
SIF_Events are reported for this object.
Figure 6.9.1-1: Authentication| | Element/@Attribute | Char | Description | Type |
|---|
| | Authentication | |
The Authentication object allows a system that stores usernames and/or passwords to share them with other applications through SIF.
The provider of the Authentication object may only support providing a username or a password, or it may support both.
The Authentication object is also able to transmit a user's network identity through SIF.
If the user has an account in a network directory system that supports LDAP, the user's distinguishedName or username is shared
to uniquely identify the user to applications that support LDAP or native network authentication options.
| |
@
 | RefId | M | The SIF RefId that uniquely identifies this authentication object. | RefIdType |
| @ | SIF_RefId | M | The SIF RefId of a student or staff member | IdRefType |
| @ | SIF_RefObject | M | The type of SIF object that the SIF_RefId attribute identifies. | values:
- StudentPersonal
- StaffPersonal
- StudentContact
- EmployeePersonal
|
| | AuthenticationInfo | M | The authentication information for one system. | |
| | AuthenticationInfo/System
| M | An identifying string for the system that supports this authentication information. | xs:normalizedString
|
| @ | Type | M | Specific type of user identification. | values:
- Network
- Application
|
| | AuthenticationInfo/Username
| O | The identification string for this user. | xs:normalizedString
|
| | AuthenticationInfo/DistinguishedName
| O | This is the distinguished name of the user in a network directory system. | xs:normalizedString
|
| | AuthenticationInfo/PasswordList
| O | Allows a provider or publisher to specify the same password using multiple algorithms, if supported. | List |
| | AuthenticationInfo/PasswordList/
Password | MR | A representation of the user's password using the given algorithm. | xs:base64Binary
|
| @ | Algorithm | M | The method used to encrypt the user's password. See the implementation details below. | values:
- base64
- MD5
- SHA1
- DES
- TripleDES
- RC2
- AES
- RSA
|
| @ | KeyName | M | The name of the key to be used for decryption of the password. Left blank for plain, encoded text (Algorithm attribute value of "base64") and hash algorithms. | xs:normalizedString
|
| | SIF_Metadata | O | | SIF_Metadata |
| | SIF_ExtendedElements | O | | SIF_ExtendedElements |
Table 6.9.1-1: Authentication6.9.1.1 Password Implementation Details
While Authentication objects transported over SIF HTTPS are typically secure in transit, SIF objects are often stored in logs and databases.
If the network infrastructure is not secure, the passwords could be subject to snooping from system users.
Because of this, the design of the Authentication object requires that passwords never be transmitted in plain text, to prevent casual viewing.
The design of this object allows passwords to be securely encrypted using a variety of encryption algorithms.
Passwords in the Authentication object can be shared in one of three ways as documented in the sections below.
6.9.1.1.1 Encoded Text
Sharing a password using encoded text is a very insecure method, because it uses a well-known algorithm and the value is not encrypted.
The only merit of using this method is that the password is not readable as plain text, and thus deters any casual attempt to read a password.
To share passwords in this manner, the following steps must be followed:
-
The publishing agent creates a
Password element with the algorithm set to base64.
- The agent encodes the Unicode representation of the password using the UTF-8 encoding.
- The resulting binary value is then base64 encoded.
-
Write the result as the payload of the
Password element.
6.9.1.1.2 Hashed Text
Sharing a hashed text version of a password means that the original password is not shared.
Clear text passwords are not retrievable from values stored as hashes.
These hashed values can only be used to verify passwords input by a user.
What is shared is a cryptographically secure hash of the password.
This hash allows other applications to verify a user's password when s/he logs in by comparing the hash value, not the original password.
To share passwords in this manner, the following steps must be followed:
-
The publishing agent creates a
Password element with the algorithm set to MD5 or SHA1.
- The agent encodes the Unicode representation of the password using the UTF-8 encoding.
- Hash the resulting binary value with the chosen hash algorithm.
- Encode the binary result using base64 encoding.
-
Write the result as the payload of the
Password element.
6.9.1.1.3 Encrypted Text
Sharing a password using encrypted text can be very secure.
The key being used to encrypt the data should be known only to the applications.
The KeyName attribute is used to allow agents to uniquely identify keys that are being used.
To share passwords in this manner, the following steps must be followed:
-
The publishing agent creates a
Password element with the algorithm set to DES, TripleDES, RC2, or AES.
- The agent encodes the Unicode representation of the password using the UTF-8 encoding.
- Generate a cryptographically secure Initialization Vector (IV).
- Configure the encryption algorithm to use a cipher mode of CBC.
- Configure the encryption algorithm to use a block size of 64 bits (8 bytes).
- Configure the encryption algorithm to use the generated IV.
- Configure the encryption algorithm to use the specified key for encryption.
- Configure the encryption algorithm to use PKCS#7/PKCS#5 padding mode.
- Encrypt the binary representation of the password that was generated in step 2.
- Encode the binary result using base64 encoding.
-
Write the result as the payload of the
Password element.
6.9.1.1.3.1 Example Keys
The XML in the Authentication example can be used to verify an agent's implementation of any of the published algorithms.
The password being shared for the sake of the example is ¿sècrèt.
High-Unicode characters are being used in this example to validate proper encoding.
The actual Unicode characters are: U+00BF, U+0073, U+00E8, U+0063, U+0072, U+00E8, U+0074.
The encryption keys being used are as follows (in base 64 format)
| Key Name | Key (in base64 format) |
| 64-BIT_KEY | dW7SKzwdn0Q= |
| 128-BIT_KEY | TcdilmUZ6qvbmegl2it2pA== |
| 192-BIT_KEY | mECbXMo+fOMWRwam7tyUEE59jbO9O0Z4 |
NOTE: Real-world implementations of password sharing should use keys other than the ones used for this documentation.
These keys are provided for example's sake only.
Keys should be generated using a secure cryptographic key generator.
<Authentication RefId="4286194F43ED43C18EE2F0A27C4BEF86" SIF_RefId="23B08571E4D645C3B82A3E52E5349925" SIF_RefObject="StudentPersonal">
<AuthenticationInfo>
<System Type="Network">NetworkSystem</System>
<Username>User01</Username>
<DistinguishedName>cn=User01, cn=Users, dc=sifinfo, dc=org</DistinguishedName>
<PasswordList>
<Password Algorithm="SHA1" KeyName="SHA1">1zKHIKRoPb3y0gZLJnFhQspdevg=</Password>
<Password Algorithm="MD5" KeyName="MD5">IwErjiNuanYLAmyFwyulPg==</Password>
<Password Algorithm="base64" KeyName="BASE64">wr9zw6hjcsOodA==</Password>
<Password Algorithm="DES" KeyName="64-BIT_KEY">6XSjrzAgkrd41Nzb61w5vwuqzKsQbybL</Password>
<Password Algorithm="RC2" KeyName="128-BIT_KEY">jqCzWFS38Xs7tx7v2ksa01TrFhBnixI8</Password>
<Password Algorithm="TripleDES" KeyName="192-BIT_KEY">msf17ucBbhN44uJpXTGGfI3twSR/cS/u</Password>
</PasswordList>
</AuthenticationInfo>
</Authentication>
6.9.2 SIF_LogEntry
This object captures an occurrence within a SIF node (ZIS or agent)—error, warning or information—for storage in an optionally provided zone log.
SIF_LogEntry Adds are reported and are used to post new log entries to the provider of the log.
Of course, subscribing agents may also filter incoming Adds as part of their own logging mechanism.
Any Change or Delete SIF_Events should be ignored at the agent level, but should be routed by the
ZIS (though this should not be necessary). Use of the log is optional and voluntary, except where noted as mandatory in this specification.
Nodes may post as much or as little log data as required with the expectation that if there is a provider of SIF_LogEntry that the logged entries be available
for a provider-defined amount of time subject to provider-defined restrictions on the quantity of data
logged by any given node.
SIF_Events are reported for this object.
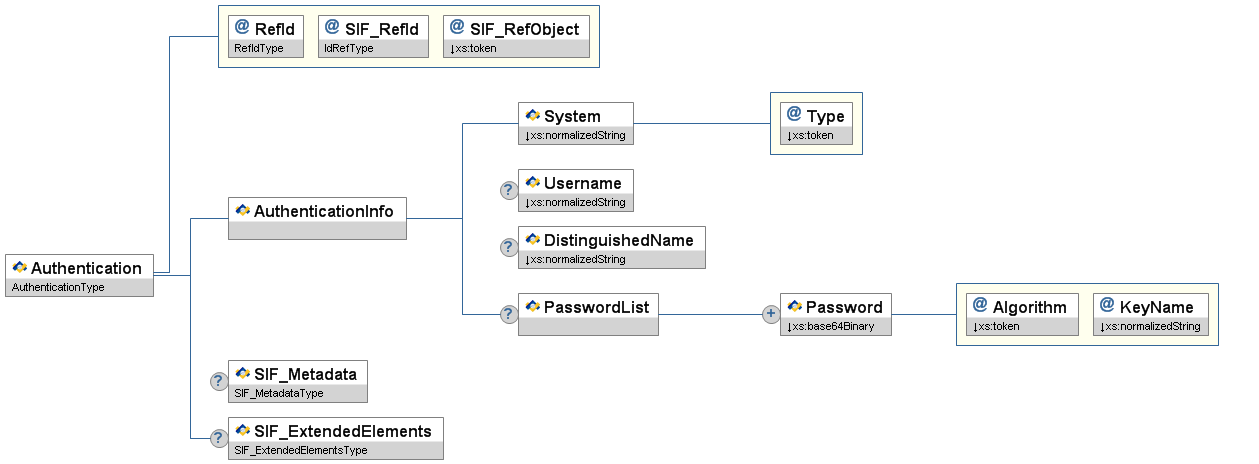
Figure 6.9.2-1: SIF_LogEntry| | Element/@Attribute | Char | Description | Type |
|---|
| | SIF_LogEntry | |
This object captures an occurrence within a SIF node (ZIS or agent)—error, warning or information—for storage in an optionally provided zone log.
SIF_LogEntry Adds are reported and are used to post new log entries to the provider of the log.
Of course, subscribing agents may also filter incoming Adds as part of their own logging mechanism.
Any Change or Delete SIF_Events should be ignored at the agent level, but should be routed by the
ZIS (though this should not be necessary). Use of the log is optional and voluntary, except where noted as mandatory in this specification.
Nodes may post as much or as little log data as required with the expectation that if there is a provider of SIF_LogEntry that the logged entries be available
for a provider-defined amount of time subject to provider-defined restrictions on the quantity of data
logged by any given node.
| |
| @ | Source | M | The SIF node that logged this entry. | values:
- Agent
- ZIS
|
| @ | LogLevel | M | The level of the log entry herein described. | values:
- Info
- Warning
- Error
|
| | SIF_LogEntryHeader | M |
This is a copy of the SIF_Event/SIF_Header in the message that added this SIF_LogEntry to the zone.
This copy facilitates querying log entries with regard to source, time, optionally destination, etc.
| |
| | SIF_LogEntryHeader/SIF_Header
| M | | SIF_Header |
| | SIF_OriginalHeader | O |
If this log entry references a previous SIF_Message,
this element contains a copy of the referenced message's SIF_Header.
| |
| | SIF_OriginalHeader/SIF_Header
| M | | SIF_Header |
| | SIF_Category | C | A SIF_LogEntry category. May be omitted for informational-type postings, where typically a textual description will suffice.
Note that categories may be combined with the Source attribute of SIF_LogEntry to differentiate agent error conditions from ZIS error conditions.
| values:
- 1
- Success
- 2
- Data Issues with Success Result
- 3
- Data Issues with Failure Result
- 4
- Error Conditions
|
| | SIF_Code | O | A SIF_LogEntry code with regard to SIF_Category above. May be omitted for informational-type postings, where typically a textual description will suffice. If a SIF_Code is included, SIF_Category must be included as well. | union of:
SIF_LogEntrySuccessCategoryType
SIF_LogEntryDataIssuesWithSuccessResultType
SIF_LogEntryDataIssuesWithFailureResultType
SIF_LogEntryAgentErrorConditionType
SIF_LogEntryZISErrorConditionType |
| | SIF_ApplicationCode | O |
An error code specific to the application posting the entry.
Can be used by vendors to query log entries for errors specific to their applications.
If a SIF_ApplicationCode is included, SIF_Category must be included as well;
i.e., application-specific error codes should fall within one of the defined log entry categories.
| xs:normalizedString
|
| | SIF_Desc | M | A textual description of the error. | xs:string
|
| | SIF_ExtendedDesc | O | Any extended error description. | xs:string |
| | SIF_LogObjects | O | | List |
| | SIF_LogObjects/SIF_LogObject
| MR | Any SIF data objects to which this log entry may apply. | SIF_ResponseObjectType |
| @ | ObjectName | M | The name of the SIF object referenced (e.g. StudentPersonal). | SIF_RequestObjectNamesType |
| | SIF_Metadata | O | | SIF_Metadata |
| | SIF_ExtendedElements | O | | SIF_ExtendedElements |
Table 6.9.2-1: SIF_LogEntry
<SIF_LogEntry Source="Agent" LogLevel="Error">
<SIF_LogEntryHeader>
<SIF_Header>
<SIF_MsgId>83252CE5C5F14FD88607F645224E4CAA</SIF_MsgId>
<SIF_Timestamp>2006-08-19T10:36:00-05:00</SIF_Timestamp>
<SIF_SourceId>RamseySISAgent</SIF_SourceId>
</SIF_Header>
</SIF_LogEntryHeader>
<SIF_Category>4</SIF_Category>
<SIF_Code>1</SIF_Code>
<SIF_Desc>Agent has run out of memory and will shut down</SIF_Desc>
<SIF_ExtendedDesc>OutOfMemoryException: ...</SIF_ExtendedDesc>
</SIF_LogEntry>
<SIF_LogEntry Source="Agent" LogLevel="Error">
<SIF_LogEntryHeader>
<SIF_Header>
<SIF_MsgId>BA86894B795A4EB7A45093AD1CDBA54C</SIF_MsgId>
<SIF_Timestamp>2006-08-19T10:39:00-05:00</SIF_Timestamp>
<SIF_SourceId>RamseySISAgent</SIF_SourceId>
</SIF_Header>
</SIF_LogEntryHeader>
<SIF_OriginalHeader>
<SIF_Header>
<SIF_MsgId>74234DCB460A4BCB8937B07467EA73CC</SIF_MsgId>
<SIF_Timestamp>2006-08-19T10:29:00-05:00</SIF_Timestamp>
<SIF_SourceId>RamseyLibraryAgent</SIF_SourceId>
</SIF_Header>
</SIF_OriginalHeader>
<SIF_Category>3</SIF_Category>
<SIF_Code>2</SIF_Code>
<SIF_ApplicationCode>-33</SIF_ApplicationCode>
<SIF_Desc>Could not delete student John Smith due to business rule</SIF_Desc>
<SIF_LogObjects>
<SIF_LogObject ObjectName="StudentPersonal">
<StudentPersonal RefId="76D3A70232FE40D7A5D43A7A317EAEF9">
<AlertMessages>
<AlertMessage Type="Legal">This is the Legal Alert for Joe Student</AlertMessage>
</AlertMessages>
<LocalId>P00001</LocalId>
<StateProvinceId>WB0025</StateProvinceId>
<ElectronicIdList>
<ElectronicId Type="Barcode">206654</ElectronicId>
</ElectronicIdList>
<Name Type="04">
<LastName>Student</LastName>
<FirstName>Joe</FirstName>
<MiddleName />
<PreferredName>Joe</PreferredName>
</Name>
<Demographics>
<Gender>M</Gender>
</Demographics>
<AddressList>
<Address Type="0123">
<Street>
<Line1>6799 33rd Ave.</Line1>
<StreetNumber>6799</StreetNumber>
<StreetName>33rd</StreetName>
<StreetType>Ave.</StreetType>
</Street>
<City>Chicago</City>
<StateProvince>IL</StateProvince>
<Country>US</Country>
<PostalCode>60660</PostalCode>
</Address>
</AddressList>
<PhoneNumberList>
<PhoneNumber Type="0096">
<Number>(312) 555-1234</Number>
</PhoneNumber>
</PhoneNumberList>
<EmailList>
<Email Type="Primary">Joe.Student@anyschool.com</Email>
</EmailList>
<OnTimeGraduationYear>2007</OnTimeGraduationYear>
</StudentPersonal>
</SIF_LogObject>
</SIF_LogObjects>
</SIF_LogEntry>
<SIF_LogEntry Source="Agent" LogLevel="Info">
<SIF_LogEntryHeader>
<SIF_Header>
<SIF_MsgId>64B0CC6CFB314A328E520A102229CBC8</SIF_MsgId>
<SIF_Timestamp>2006-08-19T10:46:00-05:00</SIF_Timestamp>
<SIF_SourceId>RamseySISAgent</SIF_SourceId>
</SIF_Header>
</SIF_LogEntryHeader>
<SIF_Desc>Agent starting synchronization</SIF_Desc>
</SIF_LogEntry>
<SIF_LogEntry Source="ZIS" LogLevel="Error">
<SIF_LogEntryHeader>
<SIF_Header>
<SIF_MsgId>BC1D982CEC5F49D998169930FE5B271C</SIF_MsgId>
<SIF_Timestamp>2006-08-19T10:49:00-05:00</SIF_Timestamp>
<SIF_SourceId>RamseyZIS</SIF_SourceId>
</SIF_Header>
</SIF_LogEntryHeader>
<SIF_OriginalHeader>
<SIF_Header>
<SIF_MsgId>74234DCB460A4BCB8937B07467EA73CC</SIF_MsgId>
<SIF_Timestamp>2006-08-19T10:29:00-05:00</SIF_Timestamp>
<SIF_SourceId>RamseyLibraryAgent</SIF_SourceId>
</SIF_Header>
</SIF_OriginalHeader>
<SIF_Category>4</SIF_Category>
<SIF_Code>2</SIF_Code>
<SIF_Desc>Could not deliver StudentPicture Add to RamseyLibraryAgent (127,546 bytes) due to maximum buffer size of 16,384 bytes.</SIF_Desc>
</SIF_LogEntry>